The Idea
We tend to associate secure passwords with complicated and hard-to-remember passwords. But it doesn't have to be this way.
We make password difficult to guess by increasing entropy — the degree of uncertainty in the password. The higher the entropy, the harder it is to guess the password.
One way of increasing entropy is to make passwords more complicated. Another way is to make the password longer, but keeping it simple, as the following xkcd comic shows:
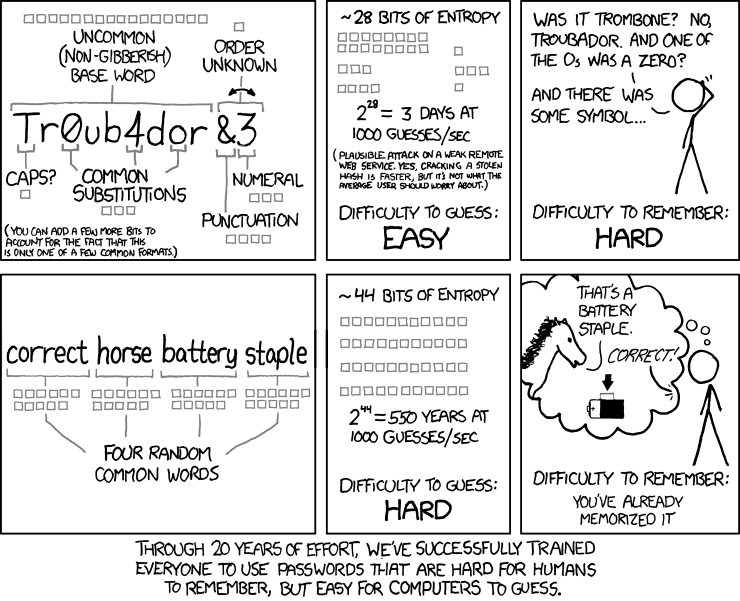
The core idea is that while using a single dictionary word as a password is horribly insecure and can be cracked in seconds, each additional word makes cracking exponentially harder.
There is a lot of criticism on the internet about this password scheme. However, most of them fail to get the actual point. There are also claims that correcthorsebatterystaple is as secure as a 9 character password, which sounds fairly bad. This is true if your 9 character password is truly random, such as n98idhi3n, and not say, Tr0ub4d0r. The point is that, correcthorsebatterystaple is more memorable than n98idhi3n, for approximately equal security. To increase security, we can always add more words.
5 words from the large list, or 6 words from the small list is sufficient for all reasonable threats.
Let us consider the absolute worst case, assuming the attacker knows your password is generated by this site, knowing that it has 65 bits of entropy, your password was insecurely hashed, and your enemy has GPUs to run 500 billion attempts every second. Even then, this scheme will resist the cracking attempt for over a year.
Running this sort of attack is prohibitively expensive. Unless you possess highly valuable secrets that makes this sort of effort worthwhile (you should use something more secure than passwords in such a case), you don't have to worry about this hypothetical scenario. If you have to, you can simply add more words.
In practice, most real life systems use secure password hashing algorithms, captchas, and other mechanisms to stop password cracking. It is unlikely that your attacker can reach anywhere close to a million guesses a second, and so a four word password (from the large list) is probably sufficient in real life. If you are paranoid and want to feel better, use five.